
Top Zero Trust Implementation Considerations
The concept of Zero Trust has become a beacon of security strategy in all major companies. It’s all about one simple principle: trust no one or nothing until they’ve proven themselves. But amidst the buzz, implementing Zero Trust isn’t a one-size-fits-all approach. Each organization must follow its unique path.
In this article, we’ll break down the top considerations for implementing Zero Trust, providing technical insights to guide your journey toward enhanced security.
How do you Implement Zero Trust?
Implementing a zero-trust security model involves a number of key steps and practices to ensure complete protection of resources:
1. Identify and classify data: Determine sensitive data and categorize it based on importance.
2. Define security perimeters: Establish clear boundaries for network and asset security.
3. Enforce strict access controls: Authenticate and monitor all resource access continuously.
4. Implement micro-segmentation: Create smaller, secure network segments to protect sensitive assets.
5. Monitor and log all activity: Utilize logging systems to track user actions and system events.
6. Automate policy enforcement: Use automation to enforce access policies and respond to incidents in real time.
7. Regularly assess and improve security: Continuously evaluate security posture and enhance defenses against emerging threats.
Additionally, organizations can use specific principles and technologies to enhance zero-trust implementation:
1. Deploy SASE: Utilize SASE solutions for centralized, cloud-native security.
2. Utilize Microsegmentation: Split security perimeters into smaller zones to control access more granularly.
3. Use MFA: Require multiple authentication factors for user validation.
4. Implement the Principle of Least Privilege: Limit user and resource access to the minimum necessary.
5. Validate All Endpoint Devices: Verify devices before granting access to resources to ensure compliance.
What are some Zero-Trust Implementation Challenges?
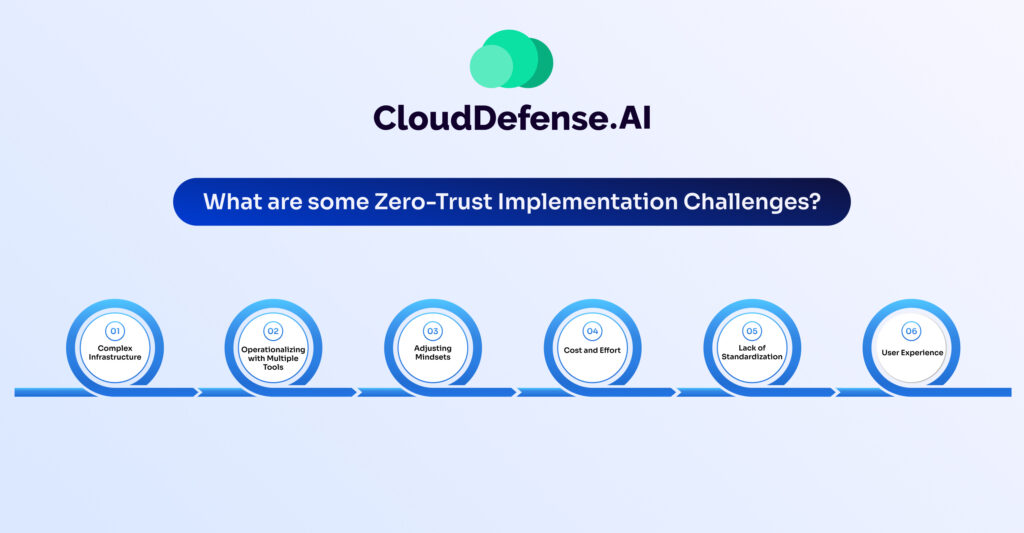
Implementing a zero trust security model presents several challenges that organizations must address:
1. Complex Infrastructure: Managing security across diverse infrastructure components, including on-premises systems, cloud services, and legacy applications, can be daunting. Ensuring consistent protection in this heterogeneous environment is challenging.
2. Operationalizing with Multiple Tools: Zero trust requires the use of various security tools, but ensuring their consistent operation across different platforms and environments can be difficult. Integration issues may arise due to the diversity of devices and systems.
3. Adjusting Mindsets: Adopting a zero trust security approach necessitates a cultural shift within the organization. Convincing stakeholders to prioritize security over convenience and embrace change can be challenging, especially in large organizations with entrenched practices.
4. Cost and Effort: Implementing zero trust requires significant investment in terms of time, resources, and finances. Designing and maintaining network segmentation, as well as hiring or training personnel, can be a resource-intensive task.
5. Lack of Standardization: The absence of industry-standard frameworks for zero trust implementation complicates efforts to ensure consistent deployment and operability across different systems and applications.
6. User Experience: Zero trust controls may impose additional authentication steps and access restrictions, potentially impacting user productivity and experience. Balancing security with usability is a key challenge.
How can Companies Accelerate Zero Trust Implementation?
To accelerate zero trust implementation, companies can implement several strategies:
1. Develop a clear plan: Establishing a well-defined plan with specific goals, timelines, and resource requirements streamlines the implementation process.
2. Conduct a comprehensive risk assessment: Identifying vulnerabilities through thorough risk assessment helps prioritize zero trust controls effectively.
3. Embrace automation: Using automation streamlines implementation reduces IT workload and enhances the accuracy and consistency of access controls.
4. Use cloud-based solutions: Cloud-based solutions such as CloudDefense.AI allow for quicker and more effective deployment of zero trust controls, especially for remote workers and third-party vendors.
5. Adopt a phased approach: Implementing zero trust in phases allows organizations to prioritize critical assets, reduce complexity, and demonstrate progress to stakeholders incrementally.
6. Invest in training and awareness: Educating employees on the importance of zero trust and providing training on relevant tools and technologies creates understanding and adoption.
7. Partner with experts: Collaborating with experienced security providers helps leverage best practices, accelerate implementation, and ensure compliance with industry regulations.
What are Some Top Considerations for Zero Trust Implementation?
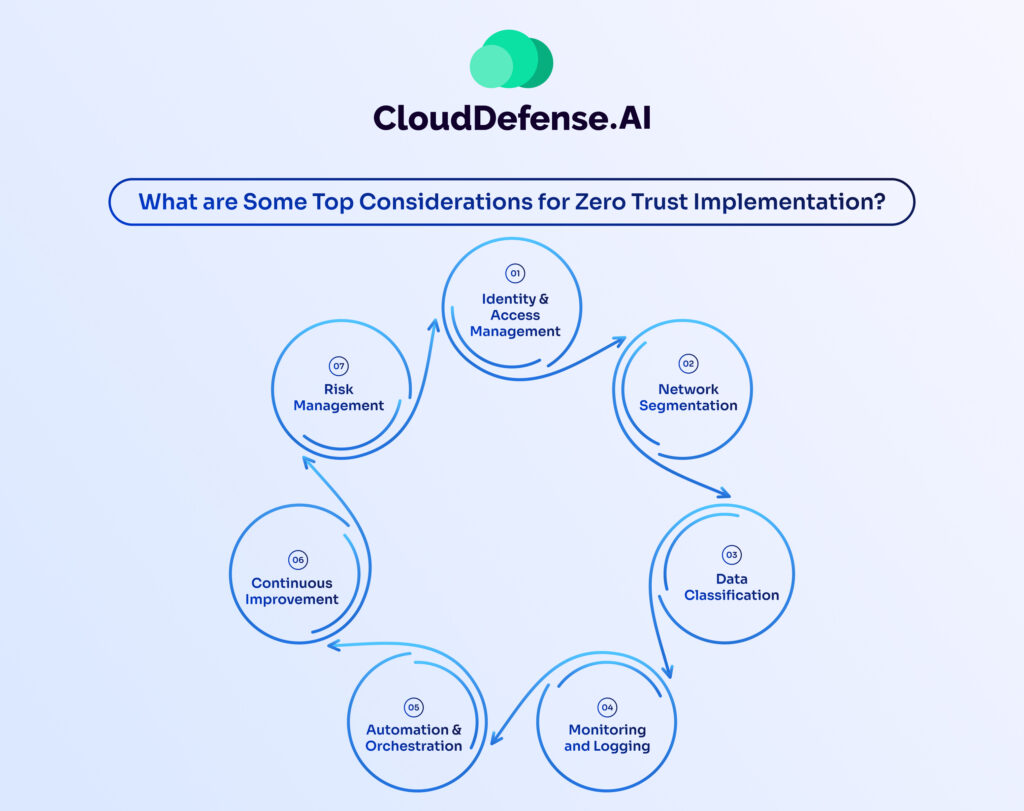
Before implementing a zero trust policy, you’d need to keep in consideration the following points:
1. Identity and Access Management: Implement strong authentication and authorization measures like MFA to ensure only authorized users access resources.
2. Network Segmentation: Create micro-segments within the network to isolate and protect sensitive resources, enhancing security posture.
3. Data Classification: Identify and classify data based on sensitivity and regulatory requirements to determine appropriate access controls.
4. Monitoring and Logging: Implement robust monitoring and logging mechanisms to track user activity, network traffic, and system events for rapid incident response.
5. Automation and Orchestration: Use automation to streamline zero trust controls across systems, reducing complexity and enhancing efficiency.
6. Continuous Improvement: Regularly assess and enhance security posture through testing, policy review, and investment in employee training and awareness.
7. Risk Management: Adopt a comprehensive risk management framework to identify, assess, and prioritize risks, establishing appropriate controls and monitoring mechanisms.
Implementing Zero Trust with AWSZeroTrustPolicy
Implementing Zero Trust with AWSZeroTrustPolicy offers organizations a powerful tool to enhance their security posture in the face of cybersecurity threats. By harnessing AWS CloudTrail logs, this open-source API generates IAM policies based on the principle of least privilege, ensuring that users access only what they need for their work.
This customized approach, focused on actual user activities within a defined timeframe, effectively reduces the attack surface, minimizes risks, and boosts overall security. Check out our repo now and contribute to AWSZeroTrustPolicy.
