What Is Zero Trust Security? The Model & Architecture
Organizations everywhere must secure large amounts of data remote employees access in cloud or hybrid setups. To tackle rising threats, the Zero Trust security model has become a strong access control system that can address vulnerabilities, stop threats, and manage data access effectively. As cyber-attacks become more common and hackers get smarter, Zero Trust Architecture provides a proactive defense strategy by following a simple rule: don’t trust anyone.
In this article, we dive deeper into everything you need about Zero Trust Architecture and explore how organizations can use this stringent security approach to strengthen their enterprise against cyber threats.
Additionally, we will examine the implementation of AWSZeroTrustPolicy, an open-source API designed to generate Zero Trust policies specifically tailored for AWS environments.
Zero Trust Architecture Explained
Zero Trust Architecture is a cybersecurity framework that revolutionizes network security by adopting a strict principle: trust no one, not even those within the organization. Unlike traditional models, ZTA continuously verifies user identity and authentication using strong identity verification methods, enhancing threat prevention at layer 7 of the network.
By limiting a user’s network access to only what's necessary for their tasks, ZTA minimizes privileges and reduces the attack surface, effectively mitigating insider threats and external attacks.
In the past, traditional security models relied on the assumption that internal actors could be trusted, leading to vulnerabilities exploited by malicious insiders.
How Does Zero Trust Security Work?
Zero Trust Security works by following a set of rules that it has established for a company to verify the identity of its users. These rules and ideas help to determine if the user is who they say they are and also verify their intent. Below is the main set of rules that Zero Trust security is built upon.
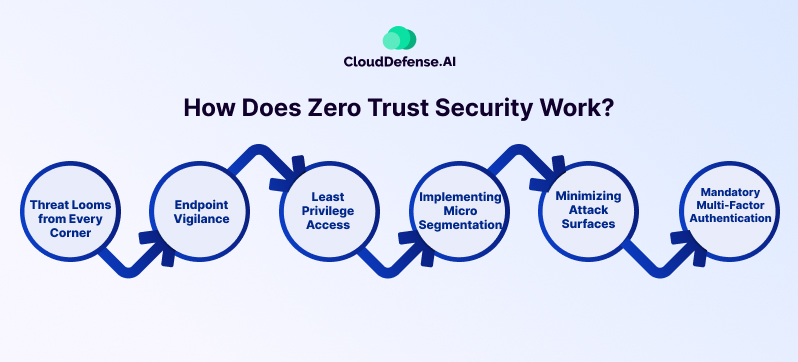
Threat Looms from Every Corner
Zero Trust acknowledges the omnipresence of potential attackers, both internal and external to the network. This perspective dictates that no device or user can be inherently trusted, requiring continuous verification.
Endpoint Vigilance
Endpoints, including devices and authenticators, are treated as untrusted entities until proven otherwise by strong security controls. Endpoint management extends to validating security measures and ensuring the secure handling of private key material.
Least-Privilege Access
Users are given just enough access for their tasks, minimizing exposure to critical network zones. This differs from traditional models that rely on broad trust or trust-but-verify methods.
Implementing Micro-Segmentation
Micro-segmentation divides network security parameters into smaller zones based on data classification, enforcing separate access controls. This ensures that users cannot traverse between zones without additional authentication.
Minimizing Attack Surfaces
Strict access controls are applied to both user and device access, effectively reducing the network's potential attack surface. Monitoring device access ensures authorization for each connection, while access control policies limit privileges to essential tasks.
Mandatory Multi-Factor Authentication
Multi-factor authentication is crucial for confirming user identities using multiple factors. Strong authentication methods surpass basic passwords by integrating hardware-based measures to prevent credential phishing and impersonation.
Core Principles of the Zero Trust Model
Zero Trust Architecture follows the principle of "Trust no one, verify everyone and everything," ensuring security measures regardless of user status.
In practice, all user traffic is routed through a proxy, enabling direct application access without the need for a network connection. This is further strengthened by these three core principles of the zero-trust model:
Identity Verification
The authentication process is initiated by subjecting user connections to identity verification, assessing "who, what, and where" to validate user identities and contextualize connection requests.
Risk Assessment and Control
Following identity verification, zero trust architecture evaluates the associated risks and applies appropriate access controls based on risk severity, ensuring secure system access.
Policy Enforcement
Security policies are rigorously enforced based on risk assessment outcomes, allowing access only when risks are deemed acceptable and in compliance with defined security protocols.
Learn more: 8 Core Principles of Zero Trust Security
Benefits of Choosing a Zero Trust Architecture
Choosing a Zero Trust Architecture offers a multitude of benefits for organizations seeking heightened security and resilience today when it comes to user authentication. This might be crystal clear to you already by now, however, we have still highlighted some key advantages that you can reap from choosing Zero Trust architecture.
|
Benefit |
Details |
|
Enhanced Security |
ZTA offers a strong defense against outside threats like phishing and malware, as well as inside risks like insider threats. By treating all users and devices with caution, ZTA shrinks the area attackers can target and sets strict rules for access. This cuts the chances of data breaches and unauthorized access. |
|
Improved Visibility and Control |
With ZTA, organizations get better insight into data access and user actions, enabling real-time monitoring. By enforcing limited access and dividing the network into smaller sections, ZTA helps organizations control access to important resources, boosting overall security. |
|
Seamless Cloud Integration |
As more organizations move to cloud-based systems, ZTA makes the transition easier by offering thorough access control and data monitoring. By applying security measures to cloud servers and apps, ZTA keeps security policies consistent across different cloud setups, lowering risks related to cloud use. |
|
Protection of Sensitive Data |
ZTA focuses on protecting sensitive data by encrypting it both when it’s stored and when it’s moving. It also sets up strict rules for who can access the data, based on how sensitive it is. By doing this, ZTA helps organizations meet regulations and keep their reputation intact. |
|
Rapid Threat Detection and Response |
ZTA uses advanced tools like machine learning and automation to spot and stop threats quickly. By always watching network traffic and how users behave, ZTA can catch and handle security problems right away, keeping breaches from causing too much harm to the organization. |
|
Regulatory Compliance |
By setting up a thorough security system, ZTA assists organizations in following regulations like PCI DSS and NIST. By improving security and protecting data, ZTA helps organizations show they’re following the rules and avoid penalties for not following them. |
What are the Types of Zero Trust?
Zero Trust architecture solutions come in two main types, as defined by Gartner:
1. Endpoint-Initiated Zero Trust Architecture
This solution involves installing agents on each user device to collect security context information. The controller then authenticates the user and allows access to approved applications through a secure gateway. While effective, this approach may be challenging to implement on unmanaged devices.
2. Service-Initiated Zero Trust Architecture
With this approach, a connector on the network establishes outbound connections to a provider cloud, where user authentication and eligibility checks take place.
Once verified, traffic is allowed to pass to the private network through the provider's cloud. This setup eliminates the need for direct access to applications and is suitable for personal user devices, although it primarily supports web applications.
Use Cases of Zero Trust
The use cases of Zero Trust Architecture span across various organizational contexts and security challenges.
- Hybrid or Remote Workforce: Organizations with remote or hybrid work environments can benefit from ZTA’s strong security measures, ensuring secure access to resources regardless of location or device.
- Legacy Systems: ZTA helps protect legacy systems by enforcing stringent access controls and monitoring user behavior, mitigating the risk of exploitation and data breaches.
- Unmanaged Devices: ZTA addresses the challenge of securing unmanaged devices by implementing endpoint security measures and enforcing access policies based on device health and user identity.
- SaaS Apps: Organizations using SaaS applications can use ZTA to enforce access controls and protect sensitive data, even in cloud-based environments.
Key Threats Addressed by ZTA
- Insider Threats: ZTA mitigates insider threats by continuously verifying user identity and monitoring user behavior, preventing unauthorized access and data exfiltration.
- Supply Chain Attacks: ZTA helps organizations protect against supply chain attacks by implementing strict access controls and monitoring third-party access to critical systems and data.
- Ransomware: ZTA enhances resilience against ransomware attacks by limiting access to sensitive resources and implementing measures to detect and mitigate threats in real time.
Relevance of ZTA for Organizations Facing
- Regulatory Requirements: ZTA helps organizations comply with industry regulations and standards by implementing security controls and maintaining audit trails to demonstrate compliance.
- Cyber Insurance Considerations: ZTA can help organizations reduce cyber insurance premiums by implementing robust security measures and minimizing the risk of data breaches and financial losses.
- User Experience: ZTA balances security with user experience by implementing adaptive authentication mechanisms and minimizing disruptions while ensuring strong security measures such as Multi-Factor Authentication (MFA).
Cybersecurity Skills Shortage: ZTA addresses the challenge of cybersecurity expertise shortage by providing a framework for implementing security controls and leveraging automated solutions to augment existing security teams.
How to implement Zero Trust Architecture in AWS
Implementing Zero Trust Architecture in cloud environments, such as AWS, is essential for organizations seeking to enhance security and minimize the risk of unauthorized access and data breaches. To effectively implement Zero Trust Architecture in AWS you can follow the steps that we have outlined below for you.
Assess Current Security Practices
Start by evaluating your organization’s current security practices and identifying areas of vulnerability, such as overly permissive access controls or reliance on seniority-based access control.
Adopt a Zero Trust Mindset
Shift towards a Zero Trust mindset by understanding that no user or device should be trusted by default, regardless of seniority or internal status. Emphasize the principle of least privilege, granting users access only to the resources they need to perform their job functions.
Utilize AWSZeroTrustPolicy
Use tools like AWSZeroTrustPolicy, an open-source AWS Policy Generator API developed by CloudDefense.AI, to implement access controls based on the principle of least privilege. This API harnesses AWS CloudTrail logs to craft IAM policies tailored to actual user activities within a specified timeframe.
Implement IAM Policies
Use IAM policies generated by AWSZeroTrustPolicy to enforce granular access controls for AWS resources. Define policies that restrict access to specific services, actions, and resources based on job roles, responsibilities, and least privilege principles.
Monitor and Audit User Activity
Implement strong monitoring and auditing mechanisms to track user activity and detect unauthorized access or suspicious behavior. Use AWS CloudTrail and AWS Config to monitor changes to IAM policies and resource configurations in real time.
Regularly Review and Update Policies
Periodically review and update IAM policies to ensure they align with evolving business needs and security requirements. Continuously assess user access patterns and adjust policies accordingly to maintain an effective Zero Trust security posture.
To Sum Up
Implementing a zero-trust policy is essential for managing user access and enhancing security against hackers. By using detailed access controls, encryption, and ongoing monitoring, organizations can strengthen their security and protect sensitive data effectively.
Check out the open-source project AWSZeroTrustPolicy on GitHub for practical implementation in AWS environments. Using this solution actively shields cloud infrastructure from both external and internal threats, ensuring overall protection against data breaches and other security risks inherent in cloud computing.
